 Are you aware of the devastating effects that cyber-attacks can have on your personal and professional life? One particular threat that has caused a lot of damage in recent years is EternalBlue.
Are you aware of the devastating effects that cyber-attacks can have on your personal and professional life? One particular threat that has caused a lot of damage in recent years is EternalBlue.
This sophisticated hacking tool was developed by the United States National Security Agency (NSA) but unfortunately, it fell into the wrong hands. Now hackers all over the world are using it to infiltrate vulnerable computer systems and cause chaos.
In this blog post, we will delve into what EternalBlue is, how it works, and most importantly – how you can protect yourself from becoming its next victim.
What is EternalBlue?
EternalBlue is a hacking tool that was developed by the NSA and used to exploit vulnerabilities in Microsoft Windows operating system. The tool was leaked online in 2017 which made it available for cybercriminals all over the world. EternalBlue allows hackers to gain access to remote computers without any authorization, allowing them to install malware or steal sensitive data.
The tool operates by taking advantage of a vulnerability in Microsoft’s Server Message Block (SMB) protocol, which is used for file sharing across networks. By sending specially crafted packets of data, EternalBlue can cause an overflow error and take control of the targeted computer remotely.
Once a hacker gains access through EternalBlue, they can use other malicious tools like ransomware or spyware to further infiltrate and damage the targeted system. In short, EternalBlue has become one of the most dangerous hacking tools on the internet today due to its ability to quickly spread throughout vulnerable networks and wreak havoc on unsuspecting victims.
How EternalBlue Works
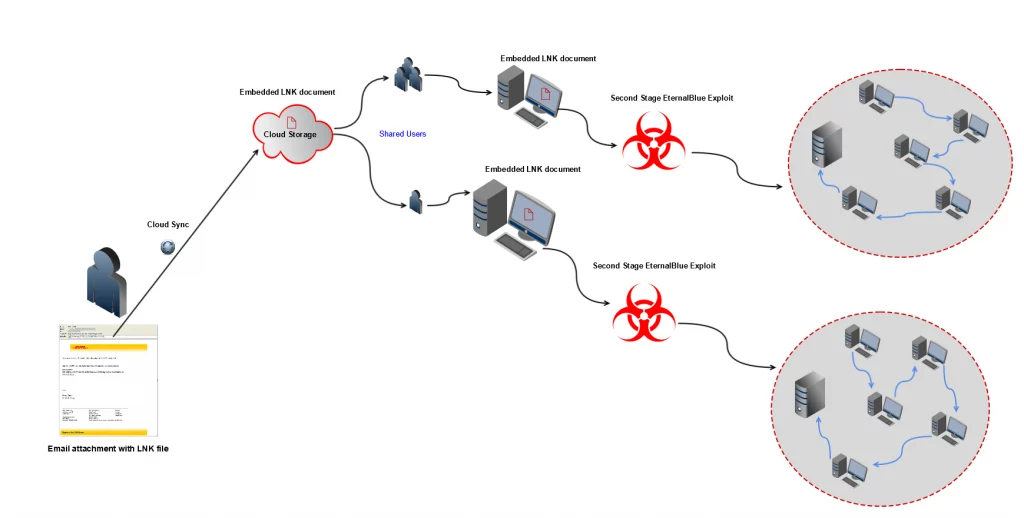 EternalBlue is a highly advanced exploit that allows hackers to gain unauthorized access to Windows systems using SMB (Server Message Block) protocol. It was developed by the NSA and leaked online in 2017, making it widely available for cybercriminals worldwide.
EternalBlue is a highly advanced exploit that allows hackers to gain unauthorized access to Windows systems using SMB (Server Message Block) protocol. It was developed by the NSA and leaked online in 2017, making it widely available for cybercriminals worldwide.
When a system is infected with EternalBlue, the malware sends malicious packets to vulnerable ports on other machines within the network. The packets contain shellcode which exploits vulnerabilities in the SMBv1 protocol used by older versions of Windows operating systems.
Once successful, EternalBlue creates a backdoor into the target system, allowing attackers full control over its operations. This can include stealing sensitive data or deploying ransomware attacks like WannaCry and NotPetya.
To prevent exploitation from EternalBlue, it’s crucial to update your operating system regularly and install patches released by Microsoft. Additionally, disabling outdated protocols like SMBv1 can also help mitigate risks associated with this exploit.
Understanding how EternalBlue works is essential for protecting yourself against this potent exploit.
The WannaCry Ransomware Attack
 The WannaCry ransomware attack was one of the most devastating cyber attacks in recent history. It affected more than 200,000 computers across 150 countries within just a few days of its release. The attack targeted computers running on Microsoft Windows operating systems that were not up-to-date with security patches.
The WannaCry ransomware attack was one of the most devastating cyber attacks in recent history. It affected more than 200,000 computers across 150 countries within just a few days of its release. The attack targeted computers running on Microsoft Windows operating systems that were not up-to-date with security patches.
The WannaCry ransomware encrypted users’ files and demanded payment in Bitcoin to unlock them. The attackers used EternalBlue exploits to spread the ransomware through networks quickly. This made it particularly difficult for organizations to contain and mitigate the damage caused by the attack.
The impact of WannaCry was felt worldwide, with major companies such as FedEx, Renault-Nissan, and Telefonica being among those hit hardest by the malware. Hospitals in the UK also suffered from severe disruptions to their services due to infected computer systems.
In response, many organizations had to increase their cybersecurity measures significantly, including updating software regularly and performing regular data backups. The WannaCry attack demonstrated how important it is for companies and individuals alike always to stay vigilant against cyber threats that are constantly evolving into more sophisticated forms.
Petya/NotPetya Ransomware Attack

The Petya/NotPetya ransomware attack is another example of the devastating effects of EternalBlue. This particular attack occurred in June 2017 and affected companies worldwide, including Maersk, a major shipping company.
The ransomware spread quickly through networks using the same vulnerability that EternalBlue exploits. Once infected, the malware encrypted files on the computer and demanded payment in Bitcoin for their release.
Unlike other ransomware attacks, however, it appears that the goal of Petya/NotPetya was not monetary gain but rather to cause destruction. The attackers behind this malware had no way to decrypt files even if victims paid the ransom.
In addition to encrypting files on individual computers, Petya/NotPetya also targeted entire network systems, making recovery difficult and costly for affected companies.
This attack highlights the need for proactive measures such as regular system updates and backups to prevent or mitigate damage from future attacks like Petya/NotPetya.
Who is behind EternalBlue?
The origin of EternalBlue can be traced back to the United States National Security Agency (NSA). It was developed as a hacking tool by their specialized unit known as Tailored Access Operations (TAO).
The purpose of developing such a powerful hacking tool was to exploit vulnerabilities in Microsoft Windows operating systems for intelligence gathering and cyber espionage. However, it wasn’t long before this sophisticated tool fell into the wrong hands.
In 2017, a group named Shadow Brokers claimed responsibility for stealing EternalBlue from NSA servers and releasing it online. This made it accessible to anyone who knew how to use it. In no time at all, hackers began using EternalBlue to launch devastating attacks on organizations worldwide.
It’s worth noting that while the original creators of EternalBlue were government agents working for national security purposes, they never intended for their work to be turned against innocent victims. Instead, it was meant only for authorized operations under strict supervision – not criminal activities perpetrated by malicious actors.
The true identity of those behind the widespread exploitation of EternalBlue remains unclear. However, what is certain is that its impact has been felt around the world and serves as a reminder that even tools created with good intentions can have dangerous consequences if they fall into the wrong hands.
How to protect yourself from EternalBlue
How to protect yourself from EternalBlue:
1. Keep your software up-to-date: Always update your operating system and security software whenever a new patch is released. This will help you stay protected against known vulnerabilities that can be exploited by EternalBlue.
2. Use strong passwords: Make sure to use complex, unique passwords for all of your accounts and change them regularly. A strong password can prevent a hacker from accessing your system through brute force attacks.
3. Disable unnecessary services: If you’re not using certain services or features on your system, disable them to reduce the attack surface available to hackers.
4. Use reputable antivirus software: Install a reputable antivirus program that includes real-time protection against malware and other threats.
5. Be cautious with email attachments: Don’t open any email attachments unless you’re absolutely sure they’re safe and trustworthy. Malware often spreads via infected email attachments, so exercise caution when opening emails from unknown senders.
6. Backup important data regularly: In case of an attack or infection, having regular backups of important data can help you recover quickly without losing valuable information.
7. Use a VPN: Whether you are at home or abroad, a VPN will disguise your real IP and keep your data safe.
By following these simple steps, you can minimize the risk of falling victim to EternalBlue or any other cyber-attack that may compromise the security of your computer systems or personal data.
Best VPN to prevent Ethernalblue attacks
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Best VPN Deal! Get HideIPVPN for $2.7/mo!
Every purchase you make comes with a 30-day money-back guarantee.
Conclusion
EternalBlue is a dangerous exploit that has caused immense damage to individuals and organizations around the world. The WannaCry and Petya/NotPetya ransomware attacks have shown just how devastating this exploit can be and why it’s crucial for everyone to take steps to protect themselves against it.
While there is no foolproof way to protect yourself from EternalBlue, implementing security best practices such as keeping your software up-to-date, using strong passwords, enabling two-factor authentication, and regularly backing up your data can significantly reduce the risk of falling victim to an attack.
It’s also essential always to remain vigilant about suspicious emails or links and never open attachments or click on links from unknown sources. By taking these steps, you’ll be better equipped to protect yourself against EternalBlue exploitation and other cyber threats that are out there. Stay safe online!



