What are Ransomware Attacks? [2022]
Last updated on July 24th, 2022 in VPN

In this article, we’ll be discussing ransomware attacks – what they are, how they work, and some of the most popular attacks that have occurred in recent years. We’ll also be giving you some tips on how to protect yourself from these types of attacks in the future.
Table of contents
Ransomware is a type of malware that encrypts a person’s files and demands a ransom be paid in order to decrypt them. Ransomware attacks usually happen when a person clicks on a malicious link or opens a malicious attachment in an email. Once the ransomware has been installed on the person’s computer, it will start encrypting their files. The person will then receive a message demanding that they pay a ransom in order to decrypt their files.
Ransomware attacks can be very costly for the victims. In some cases, the ransom demanded can be hundreds or even thousands of dollars. If the victim does not have a backup of their files, they may have no choice but to pay the ransom in order to get their files back.
Ransomware attacks are becoming more and more common. They are a serious threat to both individuals and businesses. It is important to be aware of the risks of ransomware and take steps to protect yourself from these attacks.
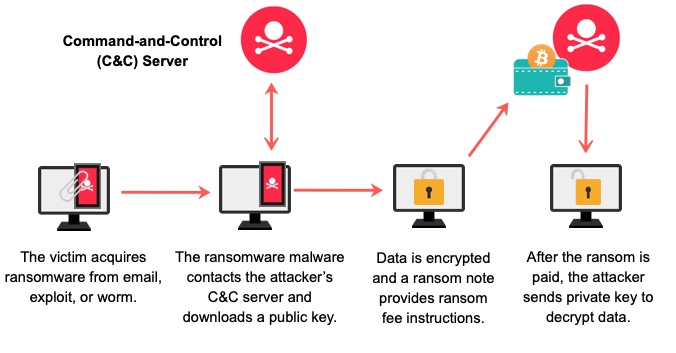
via Extrahop
Ransomware attacks are a type of cyberattack in which hackers gain access to a victim’s computer and then encrypt important files. The victim is then asked to pay a ransom, usually in the form of cryptocurrency, in order to decrypt the files and regain access to them.
There are a few different ways that ransomware attackers can gain access to a victim’s computer. One common method is through phishing emails. These emails often contain attachments or links that, when clicked, will download the ransomware onto the victim’s computer. Another method is through malicious websites. Hackers can create fake websites that look legitimate but actually contain malware. When victims visit these websites, they may inadvertently download the ransomware onto their computers.
Once the ransomware is on the victim’s computer, it will begin encrypting important files. The victim will then receive a message from the attacker demanding a ransom payment in order to decrypt the files. Ransom payments are usually made in cryptocurrency such as Bitcoin. This is because it is difficult to trace cryptocurrency transactions.
If the victim pays the ransom, the attacker will provide them with a decryption key that will allow them to decrypt the encrypted files. However, there is no guarantee that the attacker will actually provide
The most common types of ransomware are Cryptolocker, Locky, and Cerber.
 There are numerous ransomware versions, each with specific features. However, certain ransomware organizations have been more active and profitable than others, setting them apart from the competition.
There are numerous ransomware versions, each with specific features. However, certain ransomware organizations have been more active and profitable than others, setting them apart from the competition.
One of the most well-known ransomware attacks is Ryuk. This attack typically targets large organizations, and it can be devastating. Ryuk encrypts all of the files on an infected system and then demands a ransom be paid in order to decrypt the files. This can be a very costly attack, as it can take a long time to recover from.
Ryuk is often spread through phishing emails. These emails can contain attachments or links that, when clicked, will install the Ryuk ransomware on a system. Once installed, Ryuk will start encrypting files immediately. It is important to have good backups in place in case of a Ryuk attack, as it can be very difficult to decrypt the files without paying the ransom.
Ransomware attacks are a type of cyberattack in which hackers encrypt a victim’s data and demand a ransom in order to decrypt it. Maze is one type of ransomware that has been gaining popularity in recent years.
Maze ransomware works by first infecting a victim’s computer with malware. Once the victim’s computer is infected, the Maze ransomware encrypts their data. The hackers then demand a ransom from the victim in order to decrypt their data.
Maze ransomware is particularly dangerous because it not only encrypts a victim’s data, but it also steals it. This means that even if a victim pays the ransom, they may still not be able to get their data back. In addition, Maze ransomware has been known to target critical infrastructure, such as hospitals and government agencies. This can cause major disruptions and even lead to loss of life.
Overall, ransomware attacks are a serious threat to both individuals and organizations. Maze ransomware is one of the most dangerous types of ransomware due to its ability to steal data and its ability to target critical infrastructure.
1. Lockbit is a type of ransomware that encrypts files on a victim’s computer and demands a ransom be paid in order to decrypt the files.
2. Lockbit typically spreads through email attachments or malicious websites. Once it has infected a computer, it will scan the hard drive for certain types of files to encrypt.
3. Lockbit will then display a ransom note on the victim’s screen, demanding that a payment be made in order to decrypt the files. The amount of the ransom varies, but is typically around $500.
4. If the victim does not pay the ransom, their files will remain encrypted and they will not be able to access them. In some cases, victims have been able to decrypt their files without paying the ransom, but this is not always possible.
5. Ransomware attacks can be very damaging to both individuals and businesses. They can lead to loss of important data, downtime, and financial loss.
Ransomware attacks are becoming increasingly common. It is important to be aware of the dangers they pose and take steps to protect yourself from them.
DearCry is a type of ransomware that was first seen in 2020. It encrypts files on the victim’s computer and then demands a ransom be paid in order to decrypt the files. DearCry is unique in that it uses the Microsoft Cryptographic API to encrypt the files, which makes it very difficult to decrypt the files without the proper key.
DearCry has been seen targeting businesses and individuals alike. It is usually spread through email attachments or links. Once it infects a computer, it will start to encrypt various types of files, including documents, images, and videos. The ransom amount can vary depending on the number of files that have been encrypted.
If you are a victim of a DearCry ransomware attack, it is important not to pay the ransom. There is no guarantee that you will get your files back even if you do pay the ransom. Instead, you should focus on restoring your data from backups or using data recovery software to try to decrypt your files.
1. Lapsus$ is a type of ransomware attack that encrypts files on a victim’s computer and demands a ransom be paid in order to decrypt them.
2. Lapsus$ is believed to be created by a group of Russian hackers known as the Evil Corp.
3. Lapsus$ has been used in attacks against both individuals and organizations.
4. Victims of a Lapsus$ attack typically have their files encrypted with a strong cipher, making it very difficult to decrypt them without paying the ransom.
5. Lapsus$ is just one of many types of ransomware attacks that exist. Others include Cryptolocker, Locky, and WannaCry.
Another ransomware strain that targets big businesses is the REvil gang, also referred to as Sodinokibi.
One of the most well-known ransomware families online is called REvil. The ransomware organization, which has been in operation since 2019, has been behind many significant breaches, including “Kaseya” and “JBS.”
It has battled Ryuk for the distinction of most expensive ransomware version over the past few years. It is known that REvil sought $800,000 in ransom.
REvil started out as a conventional ransomware strain, but it has since developed. Now, it uses the Double Extortion method to steal data from organizations while also encrypting the files. As a result, attackers may use other methods in addition to demanding a ransom to decrypt data.
Ransomware attacks are a type of cyber attack in which hackers encrypt a victim’s data and demand a ransom payment in order to decrypt it. Ransomware attacks can be very difficult to defend against, as they often exploit vulnerabilities in a victim’s system.
One of the best ways to defend against ransomware attacks is to keep your system up-to-date with the latest security patches. This will help to close any vulnerabilities that hackers may exploit. You should also have a good antivirus program installed on your system, as this can help to detect and block ransomware attacks.
If you do become the victim of a ransomware attack, it is important not to pay the ransom. This will only encourage the attackers and may not even result in your data being decrypted. Instead, you should contact a professional who can help you to recover your data.
If you have been attacked by ransomware, the first thing you should do is disconnect your computer from the internet. This will prevent the ransomware from encrypting any more of your files. Next, you should try to restore your files from a backup. If you don’t have a backup, you may be able to use a data recovery program to recover some of your files. Finally, you should run a virus scan on your computer to remove any malicious software that may be present. For e.g. you can find tons of Kaspesrksy alternatives out there or any other antivirus for that matter.
Ransomware is a type of malware that encrypts a victim’s files and demands a ransom be paid in order to decrypt them. VPNs can help protect against ransomware attacks by encrypting traffic and providing a secure connection to the internet.
When a ransomware attack occurs, the attacker will usually target a specific type of file, such as financial documents or personal photos. They will then encrypt the files using a strong encryption algorithm. Once the files are encrypted, the attacker will demand a ransom be paid in order to decrypt them.
VPNs can help protect against ransomware attacks by encrypting traffic and hiding the IP address of the device. This makes it more difficult for attackers to target a specific device or individual. VPNs also provide a secure connection to the internet, which can help prevent data or DNS leaks if an attacker gains access to a device.
Overall, VPNs can be an effective tool for protecting against ransomware attacks. However, they are not foolproof and should be used in conjunction with other security measures, such as keeping backups of important files.
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Every purchase you make comes with a 30-day money-back guarantee.
As we move into 2022, it’s important to be aware of the dangers of ransomware attacks. These malicious attacks can cause serious damage to your computer and data, and they can be very difficult to recover from. Be sure to keep your antivirus software up to date and back up your data regularly to protect yourself from these potentially devastating attacks.