What is WebRTC Leak and How To Prevent It?
Last updated on February 16th, 2022 in VPN
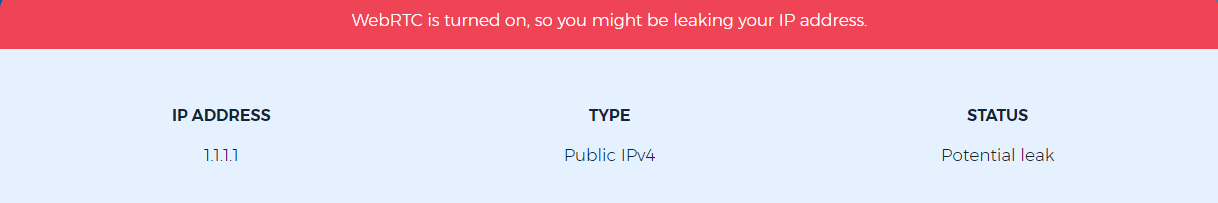
The WebRTC leak problem is a major concern for people who use VPNs and confidentiality online. We’re going to discuss what it means, how you can detect one if they happen on your end or in another person’s browser window (or even application), as well as some ways that will help keep them from happening again!
Table of contents
WebRtC transforms your browser into your own unique communication network by allowing you to include not just friends or family members but also service providers in new ways to communicate with one another. It will do this by enabling developers to build voice calling, video chat, and P2P file sharing directly into their applications without requiring end-users to sign then up for new accounts, create usernames, remember passwords, or install plug-ins.
WebRTC is about your browser becoming a gateway to real time communications using simple Javascript APIs. WebRTC does not require any server component and can be implemented with minimal overhead.
Where is the issue with WebRTC ? They use STUN/TURN servers: these are used to allow your connection to traverse NATs and firewalls. Namely, one is being used as a host to connect to (STUN), while another serves as an intermediary so that peers are not directly connecting with each other (TURN).
Web browsers are implementing WebRTC in such a way that it allows them to send requests for your local and public IP address. The results can be seen with JavaScript, making this much more accessible than other methods of accessing STUN servers which require an XMLHttpRequest process outside the normal one. This means that these requests cannot be detected in console and cannot be blocked by add-ons like AdBlockPlus or similar ones.
WebRTC is a powerful tool for browser security, but it also has some serious vulnerabilities. In particular: With Web RTC leaks sometimes devices can talk directly to each other via STUN/TURN servers; however this means that the real IP addresses of both parties will be visible in clear text – which could allow third-party websites access or even identify you as a user on their network!
This vulnerability was recently revealed by experts at Anint Group who called them “Web Rift” due to how much information gets exposed when using these kinds of all tech gadgets together seamlessly.
WebRTC Leak is the ability to discover your physical location via WebRTC protocol and see who is around us through websites or STUN/TURN servers which actually gives access all kinds of information including what gateway we use for internet access, exposing you online!
When a person’s IP address is leaked while connected to a VPN service, it makes them easier for the government or their ISP (internet provider) to track what activities they are engaged in. Not only does this defeat one purpose of using such services but also puts everyone at risk since there will now be no privacy whatsoever.
WebRTC leaks are a major concern for anyone who uses VPN services. If your IP address gets leaked during an active connection, it becomes considerably easier to track all of the websites you visit and even what apps on your phone or computer software platform may be leaking information about yourself too! Geolocation records are not just for tracking you across the internet but also give websites insight into your physical location. This means that even if you connect to a VPN, your true IP address can be requested and accessed by any site on the entire planet! So it’s important to understand WebRTC leaks and how to deal with them on each particular browser.
Testing for WebRTC leaks is extremely important, no matter the protection you are using besides that. It’s also a good idea to do it in order to make sure your VPN provider handles leaks properly. Below you will find how to easily test for WebRTC leaks:
1. Make sure no Proxy or VPN is enabled.
2. Check your IP on
BrowserLeaks doing the WebRTC test that will show you your current IP address.3. Connect to VPN.
4. Re-do step 2 by refreshing the already opened page to see if your IP has changed or is still showing the same one.
If your public IP address hasn’t changed, then we have bad news for you, your WebRTC leak test has failed and you are exposed, otherwise, you have passed it successfully and you’re protected online.
These are alternative websites for you to test WebRTC leaks:
WebRTC is a clever little technology that can be used to display video and audio between two computers without having any knowledge of what’s going on behind the scenes. That means it might show up as an IP address leak, but there are ways around this problem! For starters: if you’re using HideIPVPN or one of our browser plugins for Firefox or Chrome then we’ll block any unwanted WebRTC connections while allowing authorized ones through under your anonymous identity – just make sure all those tools are active before opening anything online so they have time build up momentum in protecting against potential vulnerabilities like these leaks.

Users of Firefox, Chrome and Opera are at risk for WebRTC leaks because these browsers have the technology-enabled by default. The same can be said about Microsoft Edge as well; however it doesn’t need any special configuration or opting into settings to do so (which means more than just about all other platforms).
If you’re always switching back and forth between various browsing apps then you need to cover all of them and make sure to test for WebRTC leaks on each of them, this way you can be sure you’ve averted potential risks.
There are two Chrome extensions known to successfully block WebRTC leaks:
uBlock Origin is the most popular and versatile Adblocker available. It not only blocks ads, trackers or malware but also provides an option to enable “WebRTC” which stops websites from loading irritating audio/video content in the background while browsing online without having any control over it whatsoever. WebRTC Network Limiter is an official Google add-on that specifically stops IP leaks without totally blocking WebRTC.
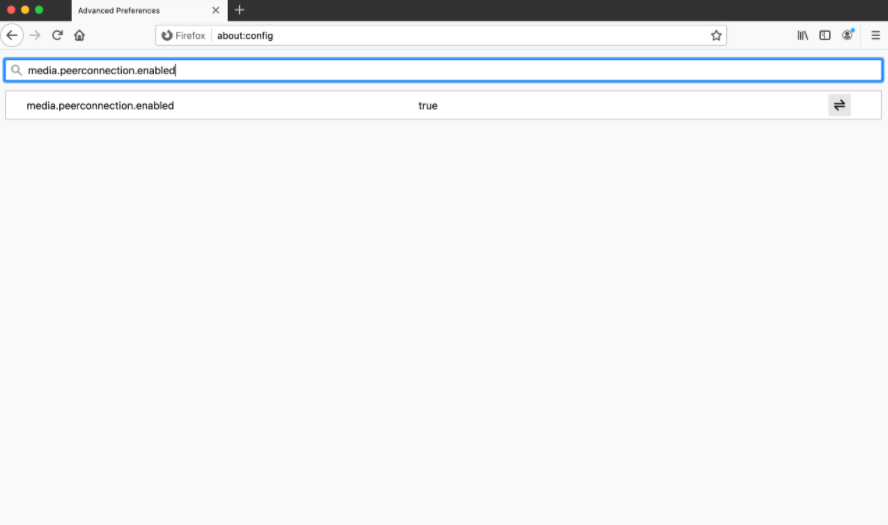
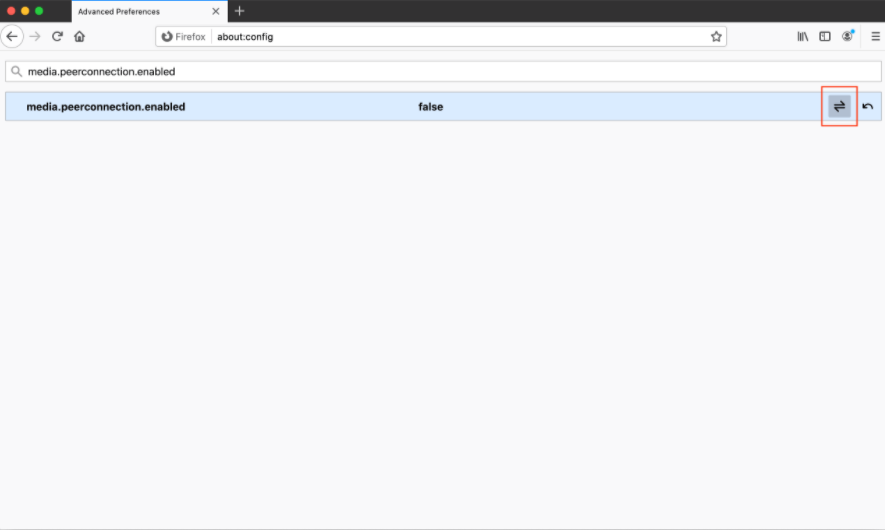
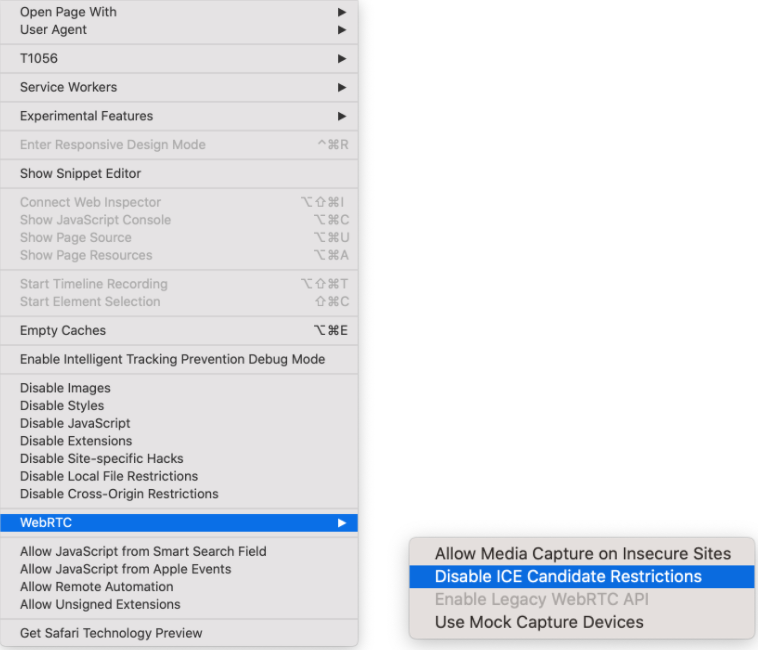
You can disable WebRTC in the browser settings by following these steps:
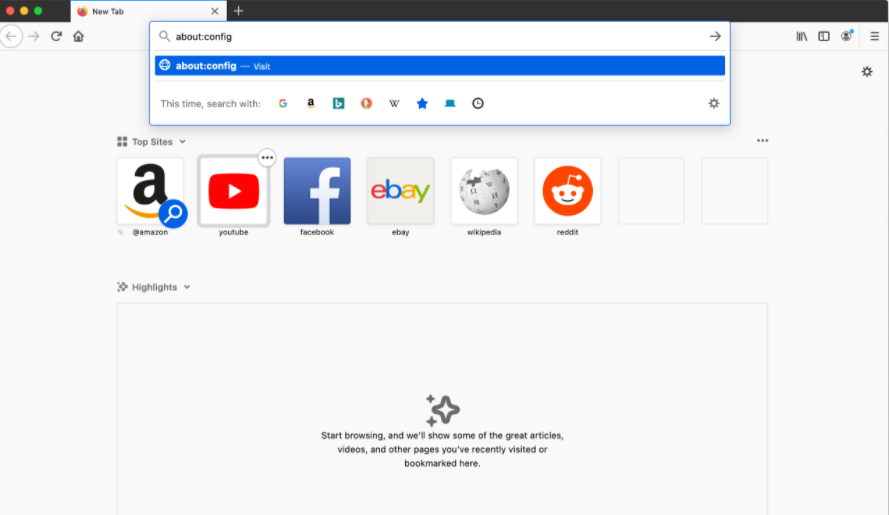
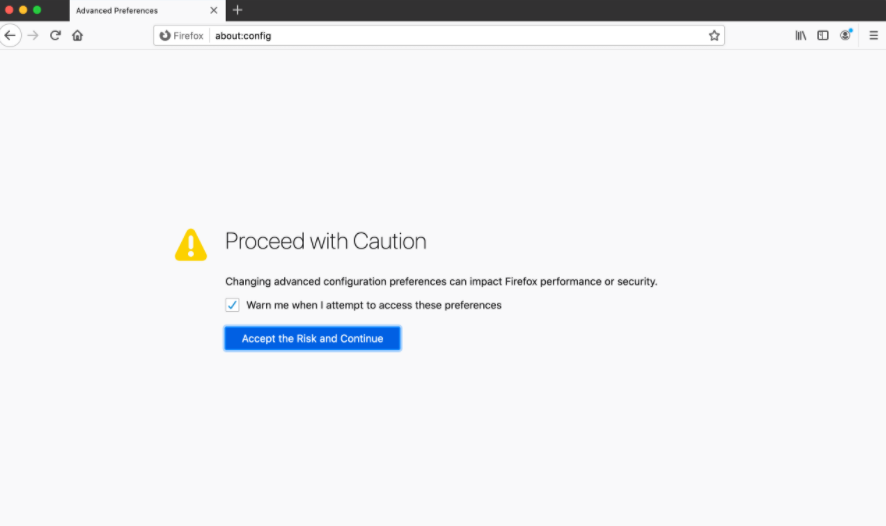
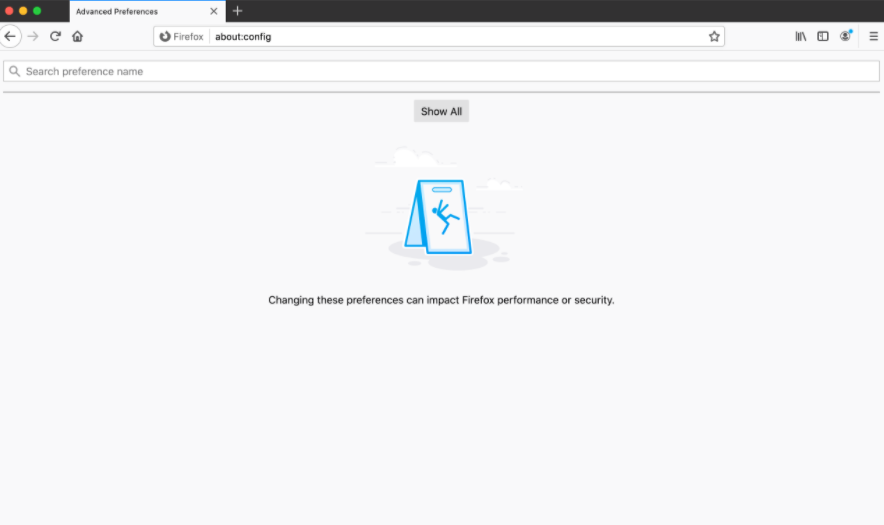
Opera does offer a built-in method to disable the WebRTC feature.
Microsoft does not allow users to disable the WebRTC feature. There are also no add-ons or hacks you can deploy to fix the vulnerability. We recommend switching to an alternative browser if possible. If you can’t, there is a single privacy setting you can use that may cut down on WebRTC leaks, though it’s far from a fix.
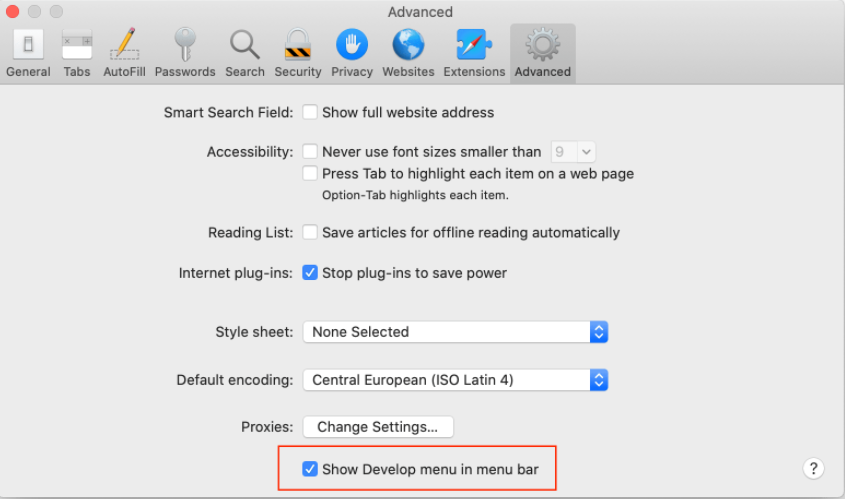
You probably won’t have to disable WebRTC in Safari. The permissions model of Safari is stricter than that implemented in most browsers. IP addresses are not made available to websites by default, except the one used to access a site. It should therefore not be necessary to take any additional actions to prevent WebRTC leaks in Safari. It should, however, be noted that if any specific site permission is granted to use video or audio capture, the IPs might be exposed.
However, you can still disable it from the browser to be extra careful.
![]()
As WebRTC leaks are becoming an increasingly big problem for users, it’s important to have a VPN that can protect you from them. Luckily HideIPVPN has created their own browser extension – currently available on Chrome and Firefox browsers- which will prevent your IP from leaking and being exposed as well as disable WebRTC on your browser. When you open new web pages while connected to HideIPVPN, your public IP addresses won’t leak.
Some browsers, however, can be aggressive when it comes to holding onto data from old tabs. If you have a tab open from before you connected to the VPN, your real IP address may be cached in memory by the browser. These IPs can persist even if you refresh the tab, which puts your privacy at risk. HideIPVPN solution takes care of this issue and let’s browse safe on the web.
HideIPVPN offers a VPN service with military-grade encryption, and high-speed servers with unlimited bandwidth.
Our service comes with shared IP addresses so that your activity can never be tied to one particular user, further protecting your privacy.
We also offer DNS leak protection, a Kill Switch, the latest VPN protocols, and a guaranteed no-log policy.
Every purchase you make comes with a 30-day money-back guarantee.
WebRTC vulnerabilities are a terrifying prospect for a lot of users, especially those who care about their online privacy. Disabling the feature in most popular browsers can be extremely easy yet not advisable as it may lead your browser into being less secure than before and give up some features that will affect how you use technology such as streaming videos or playing games online with others from around the world.
Blocking WebRTC leaks is a good start to securing your online activity, but it’s not enough. If you use HideIPVPN’s browser extension or VPN service to block these leaks, you’ll already have a collection of tools at your disposal to help you stay secure.
HideIPVPN offers a variety of useful features, including a Kill Switch to prevent unwanted data exposure. Our premium VPN can give you the best in the market internet speeds, without compromising on data encryption.
There’s never been a better time to improve your day-to-day internet safety and protect your privacy.